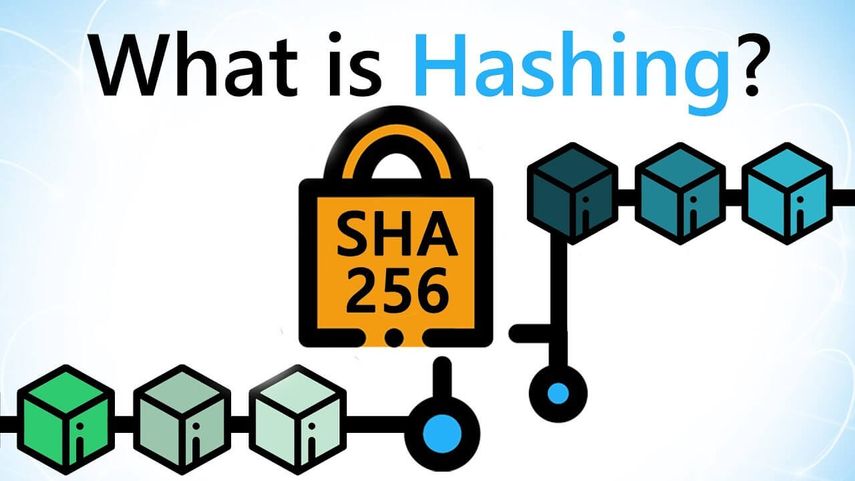
What is Hashing
A hash is a mathematical function that converts an input of arbitrary length into an encrypted output of a fixed length. Thus regardless of the original amount of data or file size involved, its unique hash will always be the same size. Moreover, hashes cannot be used to "reverse-engineer" the input from the hashed output, since hash functions are "one-way" (like a meat grinder; you can't put the ground beef back into a steak). Still, if you use such a function on the same data, its hash will be identical, so you can validate that the data is the same (i.e., unaltered) if you already know its hash.
Hashing is also essential to blockchain management in cryptocurrency.
How Hashes Work
Typical hash functions take inputs of variable lengths to return outputs of a fixed length. A cryptographic hash function combines the message-passing capabilities of hash functions with security properties.
Hash functions are commonly used data structures in computing systems for tasks, such as checking the integrity of messages and authenticating information. While they are considered cryptographically "weak" because they can be solved in polynomial time, they are not easily decipherable.
Cryptographic hash functions add security features to typical hash functions, making it more difficult to detect the contents of a message or information about recipients and senders.
In particular, cryptographic hash functions exhibit these three properties:
- They are “collision-free.” This means that no two input hashes should map to the same output hash.
- They can be hidden. It should be difficult to guess the input value for a hash function from its output.
- They should be puzzle-friendly. It should be difficult to select an input that provides a predefined output. Thus, the input should be selected from a distribution that's as wide as possible.
Because of the features of a hash, they are used extensively in online security—from protecting passwords to detecting data breaches to checking the integrity of a downloaded file.
Hashing and Cryptocurrencies
The backbone of a cryptocurrency is the blockchain, which is a global ledger formed by linking together individual blocks of transaction data. The blockchain only contains validated transactions, which prevents fraudulent transactions and double spending of the currency. The resulting encrypted value is a series of numbers and letters that do not resemble the original data and is called a hash. Cryptocurrency mining involves working with this hash.
Hashing requires processing the data from a block through a mathematical function, which results in an output of a fixed length. Using a fixed-length output increases security since anyone trying to decrypt the hash won’t be able to tell how long or short the input is simply by looking at the length of the output.
Solving the hash starts with the data available in the block header and is essentially solving a complex mathematical problem. Each block header contains a version number, a timestamp, the hash used in the previous block, the hash of the Merkle root, the nonce, and the target hash.
The miner focuses on the nonce, a string of numbers. This number is appended to the hashed contents of the previous block, which is then hashed. If this new hash is less than or equal to the target hash, then it is accepted as the solution, the miner is given the reward, and the block is added to the blockchain.
Special Considerations
Solving the hash requires the miner to determine which string to use as the nonce, which itself requires a significant amount of trial-and-error. This is because the nonce is a random string. It is highly unlikely that a miner will successfully come up with the correct nonce on the first try, meaning that the miner may potentially test a large number of nonce options before getting it right. The greater the difficulty—a measure of how hard it is to create a hash that meets the requirement of the target hash—the longer it is likely to take to generate a solution.
An Example of a Hash
Hashing the word “hello” will produce an output that is the same length as the hash for “I am going to the store.” The function used to generate the hash is deterministic, meaning that it will produce the same result each time the same input is used. It can generate a hashed input efficiently; it also makes determining the input difficult (leading to mining), as well as makes small changes to the input result in an unrecognizable, entirely different hash.
Processing the hash functions needed to encrypt new blocks requires substantial computer processing power, which can be costly. To entice individuals and companies, referred to as miners, to invest in the required technology, cryptocurrency networks reward them with both new cryptocurrency tokens and a transaction fee. Miners are compensated only if they are the first to create a hash that meets the requirements outlined in the target hash.
Frequently Asked Questions
What is a hash function?
Hash functions are mathematical functions that transform or "map" a given set of data into a bit string of fixed size, also known as the "hash value."
How is a hash value calculated?
A hash function utilizes complex mathematical algorithms that convert data of arbitrary length to data of fixed length (for instance, 256 characters). If you change one bit anywhere in the original data, the entire hash value changes, making it useful for verifying the fidelity of digital files and other data.
What are hashes used for in blockchains?
Hashes are used in several parts of a blockchain system. First, each block contains the hash of the block header of the previous block, ensuring that nothing has been tampered with as new blocks are added. Cryptocurrency mining using proof-of-work (PoW), furthermore, utilizes hashing of randomly generated numbers in order to arrive at a specific hashed value containing a series of leading zeroes. This arbitrary function is resource-intensive, making it difficult for a bad actor to overtake the network.
KEY TAKEAWAYS
- A hash is a function that meets the encrypted demands needed to solve for a blockchain computation.
- Hashes are of a fixed length since it makes it nearly impossible to guess the length of the hash if someone was trying to crack the blockchain.
- The same data will always produce the same hashed value.
- A hash, like a nonce or a solution, is the backbone of the blockchain network.
- A hash is developed based on the information present in the block header.